Wij zijn |
Stored XSS in BigBlueButton
Pentests.nl has discovered a vulnerability in BigBlueButton (version 2.4.7 and prior) which could be exploited to perform stored Cross-Site Scripting (XSS) attacks by sending private messages to users.
About BigBlueButton
BigBlueButton is an open source web conferencing system designed for online meetings and online learning. BigBlueButton is a tool used by instructors and teachers, which helps them access to Learning Management Systems, engagement tools and analytics.
Overview
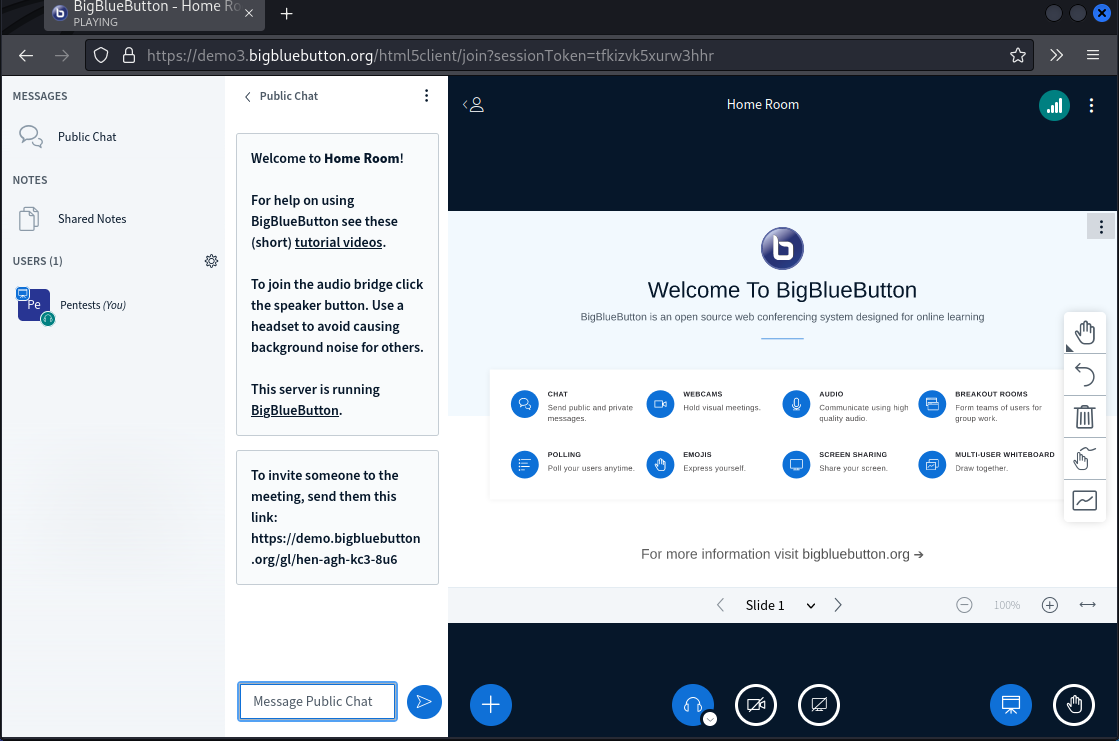
The XSS vulnerability can be triggered by joining a room with a XSS payload as username and send a private message to a user.
Impact
A successful exploit allows attackers to inject malicious JavaScript code. Doing this could lead to multiple exploitation scenarios using XSS in BigBlueButton, including adding an administrator account.
CVSS score: 7.2 High
CVSS string: 3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:N
Remediation
Update BigBlueButton to version 2.48 or 2.5.
Disclosure timeline
24-03-2022 – Bug discovered, initial report to BigBlueButton team
01-04-2022 – A reminder sent
03-04-2022 – Vulnerability acknowledgement by BigBlueButton
09-06-2022 – Private patch was released and pentests.nl verified the patch
09-06-2022 – Public patch was released for versions 2.4 and 2.5 from BigBlueButton
22-06-2022 – Full disclosure
References
https://github.com/bigbluebutton/bigbluebutton/releases/tag/v2.4.8
https://github.com/bigbluebutton/bigbluebutton/releases/tag/v2.5.0
https://github.com/bigbluebutton/bigbluebutton/security/advisories/GHSA-hwv2-5pf5-hr87
Hoe kunnen wij u helpen?
Offensive Entra ID (Azure AD) and Hybrid AD security – Outsider Security review
In this blog post, I share my personal journey and insights from undertaking the Certified Azure Red Team Expert (CARTE) certification offered by Altered Security.
The WiFi Pineapple: Basic Usage
The Wi-Fi Pineapple, developed by Hak5, is a powerful tool designed for wireless network auditing. Its versatility makes it ideal for red teamers and physical pentesters who need to assess wireless environments quickly and efficiently. In this blog post, we’ll go through the basic usage of the Wi-Fi Pineapple, explain how it works, and demonstrate its potential in a controlled test scenario.
TPM‑sniffing with Saleae logic analyzer [2025]
Learn how to use a Saleae logic analyzer to intercept TPM-chip SPI communication and extract the Volume Master Key (VMK) in this practical, step‑by‑step guide. Essential for cybersecurity professionals aiming to strengthen hardware defenses.