Wij zijn |
The WiFi Pineapple: Basic Usage
The Wi-Fi Pineapple, developed by Hak5, is a powerful tool designed for wireless network auditing. Its versatility makes it ideal for red teamers and physical pentesters who need to assess wireless environments quickly and efficiently. In this blog post, we’ll go through the basic usage of the Wi-Fi Pineapple, explain how it works, and demonstrate its potential in a controlled test scenario.

The wifi pineapple
What is the Wi-Fi Pineapple
The Wi-Fi Pineapple is a Linux-based router running custom firmware, designed to attack, sniff, or redirect clients that connect to its network. Its primary use is to exploit the “Connect Automatically” feature enabled by default on most smart devices we use in daily life.
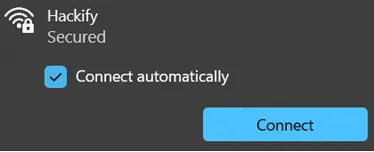
Connect Automatically button
Phones, laptops, smartwatches, and other wireless devices will often reconnect to any network they’ve previously trusted—without user interaction. The Wi-Fi Pineapple exploits this behavior using its PineAP functionality. This “Pineapple Access Point” feature allows the device to scan for nearby networks and impersonate them.
Once PineAP is active, the Wi-Fi Pineapple can:
- Trick client devices into connecting to it instead of their legitimate access point.
- Wait passively for nearby devices to automatically connect when they recognize a “known” network.
This makes it incredibly effective during red team operations, where stealth and client-side access are crucial.
Setting up
The first step in setting up the Wi-Fi Pineapple is unboxing the device and attaching the three external antennas

boxed Pineapple
To power the device, simply connect it via USB-C to a laptop, desktop, or power bank. For the initial configuration, it’s recommended to connect the Pineapple to a laptop or desktop to share the computer’s internet connection over USB.

unboxed and assembled
Once powered on, the Pineapple’s web interface can be accessed via:
After connecting with the web interface, the setup can be followed to install the firmware.
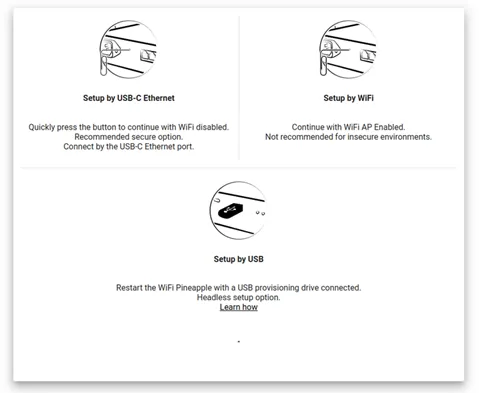
setup options
We recommend continuing the setup by Wi-Fi for easier access and mobility. However, ensure that you’re operating in a secure, controlled environment before enabling Wi-Fi-based management.
During the setup, the Pineapple will prompt to download and install the latest firmware. If using Wi-Fi setup, connect the device to a nearby access point (such as your router) to provide internet access.
Once the firmware installation is complete, the device is ready to use.
Learning the functions
The Wi-Fi Pineapple offers a wide range of features and extensions. In this section, we’ll go over its most important functions.
The WiFi Pineapple: Basic Usage
Dashboard
The Wi-Fi Pineapple features a built-in web interface that serves as the central hub for managing and operating the device. One of the core elements of this interface is the Dashboard.
From the dashboard, users can open a local web shell directly on the Pineapple. This shell gives you access to the system’s file structure and allows advanced users to run Linux commands or inspect logs without needing SSH.

local web shell in Wi-Fi pineapple interface
Navigation is handled through the left-hand sidebar, which lists the main sections of the interface. This layout allows for quick access to different modules and settings, making it easy to switch between functionality like Recon, PineAP, and Module Management.
left-hand sidebar navigation
The dashboard displays several status cards that offer real-time information about the device and its current operations. These cards typically show:
- System load and uptime
- Disk usage
- Number of connected clients
- Current module activity
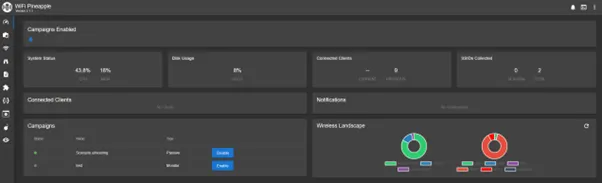
dashboard status cards
Campaigns
In the Wi-Fi Pineapple ecosystem, a campaign represents a project or engagement targeting a specific environment or device. When a red teamer initiates an attack on a wireless target, a campaign is created to structure and log the activity surrounding that operation.
Each campaign is highly customizable and can include different operating modes depending on the objective:
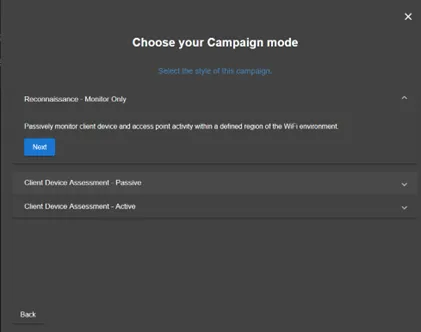
Campaign mode selects
Reconnaissance – Monitor Only
This mode performs passive observation of the wireless environment. It monitors nearby access points and client device activity without broadcasting any signals or interfering with the network. Ideal for stealthy mapping of the Wi-Fi landscape before launching further attacks.
Client Device Assessment – Passive
This mode identifies client devices that are vulnerable to basic rogue access points or Evil Twin attacks. It uses Passive PineAP mode, which only spoofs access points on-demand, based on client device requests. By adjusting the filtering rules, you can control which SSIDs the Pineapple responds to.
Client Device Assessment – Active
In this mode, the Pineapple becomes more aggressive. It uses Active PineAP to broadcast a pool of SSIDs and continuously spoof all nearby access points. This approach is effective for identifying devices that automatically connect to known networks, making them vulnerable to more advanced Evil Twin attacks.
Campaign Reporting and Automation
Campaigns can be configured to automatically generate periodic reports, offering detailed insights into captured data and activity over time. These reports can be generated at custom intervals (e.g., every 30 minutes, 3 hours, or 6 hours), depending on operational needs.
The campaign’s monitoring options can also be configured to target 2.4 Ghz networks, 5Ghz networks or both types of networks. This is especially useful if the pentester is targeting a specific laptop or phone, as phones usually only have 2.4 Ghz connections and laptops 2.4 Ghz and 5 Ghz
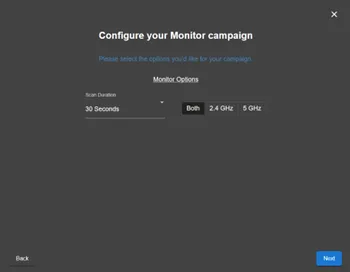
configure monitor campaign
Reports:
Using a campaign a Wi-Fi pineapple can be configured to automatically do tasks such as passive scanning or active scanning. The pineapple has the added functionality of being able to generate reports based on its scans. These reports can be generated in the HTML of JSON format.
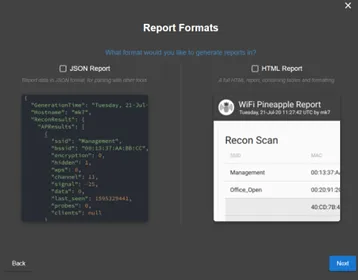
report format
Afterwords the report can be automatically exfiltrated to an email server, or uploaded using C2.
email reporting
cloud C2 exfiltration
PineAP
The PineAP module is at the core of the Wi-Fi Pineapple’s rogue access point capabilities. It enables impersonation of nearby Wi-Fi networks by broadcasting cloned SSIDs, tricking devices into connecting to fake networks. With support for both Open APs and WPA2-secured networks, it can lure users into joining unencrypted hotspots or capture partial handshakes from secured ones—useful for offline cracking attempts.
activity log of PineAP
For more advanced operations, Evil Enterprise mode allows the Pineapple to mimic WPA2-Enterprise networks, enabling the capture of authentication attempts and MSCHAPv2 hashes during login. Filters can be used to narrow the attack scope and focus only on specific clients or networks, minimizing noise and exposure.
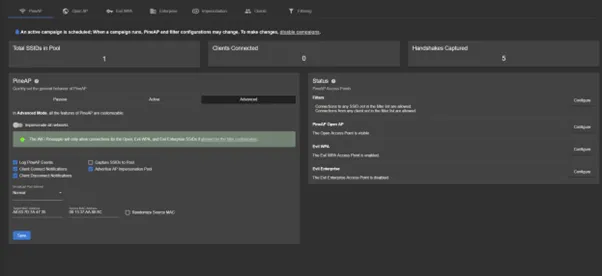
PineAP dashboard
Operating Modes
PineAP supports three distinct operational modes, giving you fine-grained control over how aggressively the device interacts with its environment:
- Passive Mode
- Collects nearby access points and client probe requests.
- Build a list of potential targets without actively broadcasting SSIDs.
- Accepts all incoming client connections.
This is ideal for stealthy surveillance or building a list of SSIDs to impersonate later.
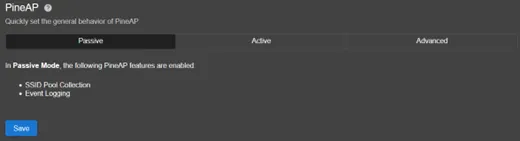
Pine AP passive mode
- Active Mode
- Actively spoofs access points seen in the area.
- Responds only to clients and SSIDs permitted by the filter list.
- Broadcasts a curated pool of fake networks.
This mode is useful for targeted impersonation attacks during controlled engagements.
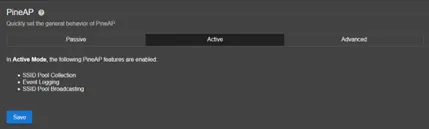
Pine AP active mode
- Advanced Mode
- Offers full manual control over PineAP features.
- You can selectively enable or disable components such as beaconing, association responses, probe replies, and logging.
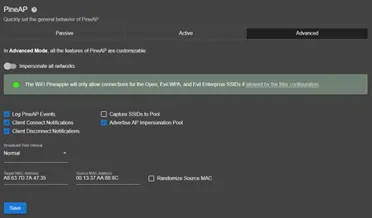
PineAP advanced mode
Recon
The Recon module is a core component of the Wi-Fi Pineapple, designed to scan and analyze the surrounding wireless landscape. It provides a real-time overview of all nearby access points and client devices, making it ideal for both initial reconnaissance and targeted attacks.
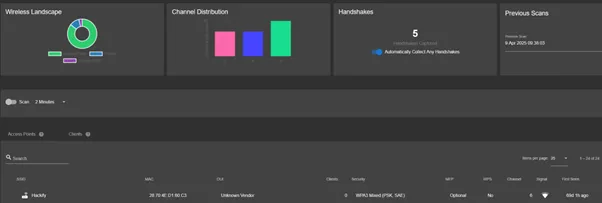
Recon scan with the Wi-Fi Pineapple
During a scan, the Recon module reveals:
- A list of access points, including SSID, BSSID, channel, encryption type, and signal strength.
- Detected client devices, including MAC addresses and the access points they are associated with.
- Protocol-specific details that help identify device types and behaviors (e.g., 802.11b/g/n/ac).
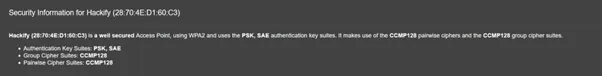
Security information of local Hackify Wi-Fi collected by the Wi-Fi Pineapple
You can configure scan duration and intensity in the settings, depending on how detailed the scan needs to be.
Targeted Attacks
Within the Recon module, the Wi-Fi Pineapple offers several active attack options that go beyond passive observation. One of the most effective is client deauthentication, which is a technique used to forcibly disconnect a device from its current access point. This exploit works on networks secured with WPA2 or lower and is commonly used to trigger a reconnection attempt.
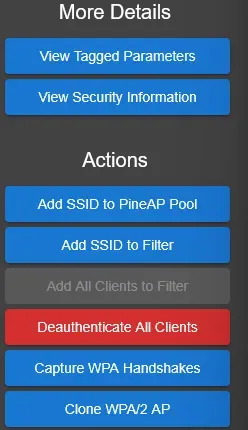
Action panel in Recon module
Deauthing a client can serve multiple purposes:
- Forcing a device to reconnect, making it more likely to connect to a rogue AP (e.g., Evil Twin).
- Creating an opportunity to capture WPA/WPA2 handshakes, which occur during the reauthentication process.
Once a client begins reconnecting, the Pineapple can intercept and save the handshake data. These WPA handshakes are stored locally and can be exported later for offline cracking using tools like hashcat or aircrack-ng. Successfully cracking a handshake may reveal the pre-shared key used by the target network.
Modules
The modules selection of the wifi pineapple is a community provided plugin marketplace. Here it is possible to download additional plugins for the Wi-Fi Pineapple which can be used in assessments:
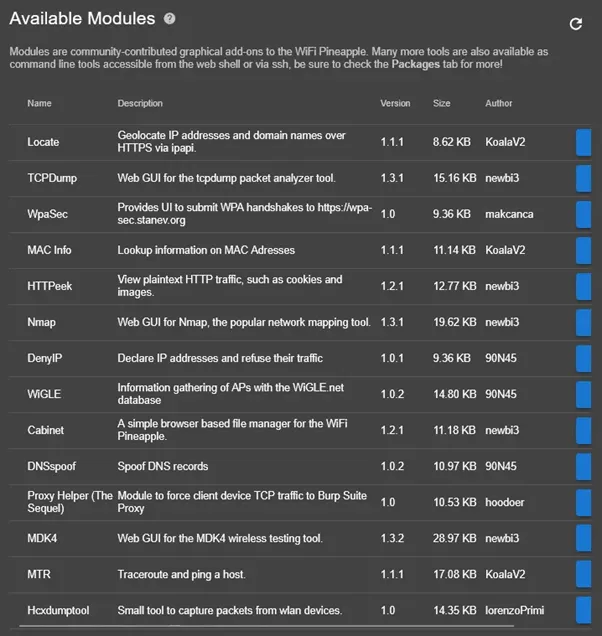
available module on the Wi-Fi Pineapple
Conclusion
modules like PineAP, Recon, and Campaigns, it enables security professionals to simulate real-world attacks such as Evil Twin, rogue access points, and WPA handshake capture—all through a streamlined and user-friendly web interface.
Thanks to its compact and discreet design, the Pineapple can be deployed in hidden or public-facing locations for extended periods. Combined with its Campaign functionality, tasks such as scanning, spoofing, and data collection can be fully automated. Results can then be exfiltrated remotely to a Cloud C2 instance or attacker-controlled server.
These features make the Wi-Fi Pineapple particularly handy in infiltrating a targets environment.
Author: Dennis Drossaert
Hoe kunnen wij u helpen?
Offensive Entra ID (Azure AD) and Hybrid AD security – Outsider Security review
In this blog post, I share my personal journey and insights from undertaking the Certified Azure Red Team Expert (CARTE) certification offered by Altered Security.
TPM‑sniffing with Saleae logic analyzer [2025]
Learn how to use a Saleae logic analyzer to intercept TPM-chip SPI communication and extract the Volume Master Key (VMK) in this practical, step‑by‑step guide. Essential for cybersecurity professionals aiming to strengthen hardware defenses.
KeyCroc (Hak5) tutorial: wat is het en hoe werkt het?
De KeyCroc van Hak5 is een fysieke aanvalstool die toetsaanslagen onderschept en zelfstandig commando’s kan uitvoeren via HID-simulatie, ook wel fysieke keylogger genoemd. In deze blog wordt toegelicht hoe de KeyCroc werkt en hoe hij geconfigureerd wordt.




